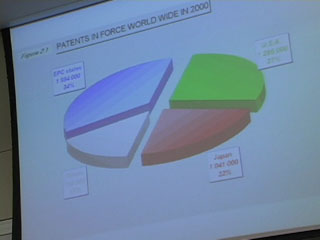
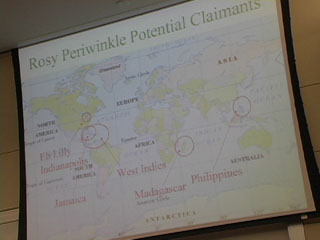
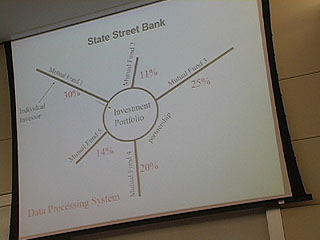
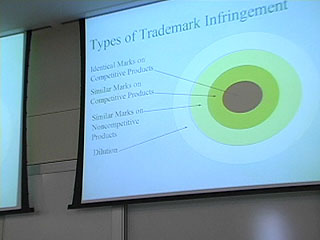
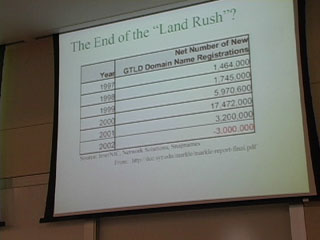
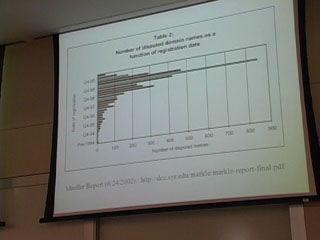
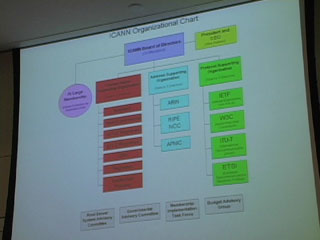
Here's Donna Wentworth on Friday, July 4, 2003, telling us what she thought of the conference.
Of course, Donna was sort of a special attendee -- she took incredible notes and posted for them in near-real time all week long.
Her favorite session (when forced to choose) was the Future of Entertainment: Music panel with the EFF's Fred von Lohmann.
My notes and 40+ pictures located below.
Terry Fisher On BMPs - Part 1 of 5 (Small - 39 MB)
Terry Fisher On BMPs - Part 2 of 5 (Small - 40 MB)
Terry Fisher On BMPs - Part 3 of 5 (Small - 36 MB)
Terry Fisher On BMPs - Part 4 of 5 (Small - 26 MB)
Terry Fisher On BMPs - Part 5 of 5 (Small - 41 MB)
More pictures underneath notes below.
Day 4 Tape 1
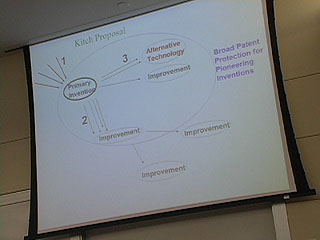
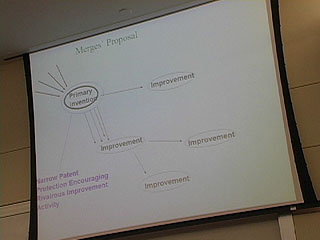
Terry - Business Method Patents
5:05 - different kinds of patents
5:34 - Examples of extensions to patents
6:31 - purified versions of naturally occurring..
10:07 - Plant Protection Act (1930) - asexually producing plants
10:42 - PVPA (1970) - sexually producing
11:09 - 1980 Chakrabarty
"Anything under the sun made by man is patentable." - Terry Fisher
12:02 - Supreme Court - also covered under utility patents
12:15 - 1954 - Atomic Weapons
12:40 - Software patents
13:30 - How surgical procedures were able to be patented
16:40 - Make doctors immune from prosecution
30:42 - Bounty Quest
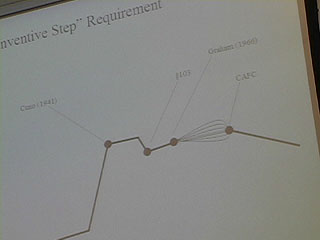
33:10 - "Inventive Step" requirement
emergence of...
34:30 - In England
35:01 - France
35:12 - Germany
36:20 - Graham Factors
40:07 - ****verify*** Aggietation for Administrative Reform
42:31 - European Initiatives
Prohibited "methods of doing business" - not allowed unless involving "technical aspect"
44:24 - European BMPs
Queue systems
45:13 - Japanese Initiatives
46:00 - "Business Method Patents are a bad idea and we should not use them at all." - Terry
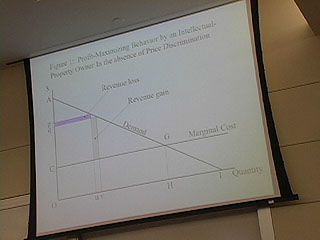
46:45 - Disadvantages of IPR
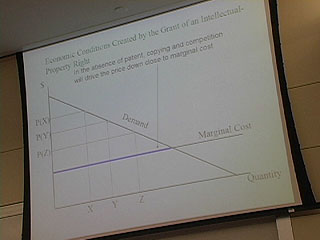
48:00 - Mousetrap example
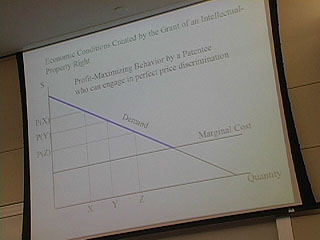
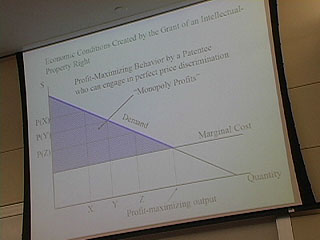
50:25 - perfect price disc
Profit maximizing behavior by a rational monopolist
55:30 - people die because of profits
Day 4 - Tape 2
2:29 - Why Business Method Patents are bad
People innovate in Business anyway
Little, if any demonstrative benefits
Increased transaction costs:
-two examiners etc.
-large dead weight losses
-consumers priced out of the market
6:00 Q and A
8:29 Reward Theory
My pythagorus question here
20:00 - How do you define them? (Business Method Patents)
This panel had the EFF's Fred von Lohmann, Charlie Nesson and Leslie L. Vadasz, Director Emeritus, Intel Corporation on it and was hosted by Jonathan Zittrain.
Music Law Panel - Part 1 of 5 (Small - 49 MB)
Music Law Panel - Part 2 of 5 (Small - 50 MB)
Music Law Panel - Part 3 of 5 (Small - 51 MB)
Music Law Panel - Part 4 of 5 (Small - 51 MB)
Music Law Panel - Part 5 of 5 (Small - 65 MB)
Below: Charlie Nesson (left), Leslie L. Vadasz (middle) and the EFF's Fred von Lohmann (right)

Below: Leslie L. Vadasz (left) and the EFF's Fred von Lohmann (right)

Day 3 Tape 7
5:45 - Fred
9:20 CD singles never sold anyway
19:48 Fred - in the rush to save the pirates?
20:49 - Charlie
29:00 Trusted computing - my question
52:45 Report
53:48 Barton
****
Tape 8
8:19 - Interdiction (Charlie)
14:20 - illegal DDOS
Fred!
Here's an interview with Reshmi Sarkar of IT for Change about the conference and what she learned there.
Reshmi Sarkar At ILAW 2003 (Small - 7 MB)
Larry explains this session best in his own words:
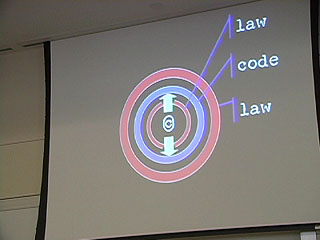
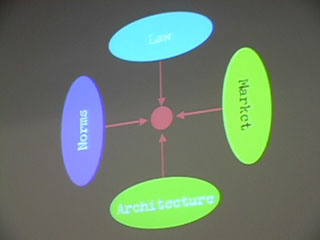
"Okay, so. We've talked a little bit this morning about the technology affecting content distribution.Terry gave you, as is typical with Terry, an extrordinary breadth of knowledge about the law affecting content distribution. And what I want to do today in this afternoon's session is to draw together something about that technology and the story about law and the story about the market to give you some idea of what transformation has occured here. A picture of a change that is hard to see unless you synthesize these three different perspectives of "technology," "law" and "the market."
After Larry talks for awhile, he gives the stage back to Terry to elaborate for a bit on a new possible system for paying artists for file sharing distribution of their works.
Larry/Terry On Technology, Law and The Market - Part 1 of 5 (Small - 53 MB)
Larry/Terry On Technology, Law and The Market - Part 2 of 5 (Small - 36 MB)
Larry/Terry On Technology, Law and The Market - Part 3 of 5 (Small - 35 MB)
Larry/Terry On Technology, Law and The Market - Part 4 of 5 (Small - 29 MB)
Larry/Terry On Technology, Law and The Market - Part 5 of 5 (Small - 33 MB)
Day 3 Tape 5 -- Larry
Before this Disney/Steamboat Bill
16:38 - Statute of Anne
17:55 - Extension of copyright term
21:00 - Changes in scope
26:30 - shift to covering previously unregulated uses
29:00 - How technology
30:30 - E books. Larry's book - "can't read aloud."
33:30 - AIBO Dog
34:00 - How DMCA hurts fair use
38:06 - Norman Lear - all in the family
40:30 - Never before has culture been in the hands of so few
44:30 - Eldred case
47:51 - PDEA
54:00 - CC info
Day 3 Tape 6
Rest of Larry
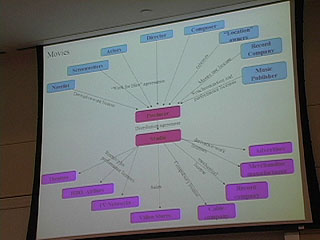
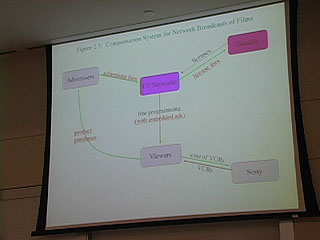
Terry on alternatives for paying artists
8:50 Responses to public goods problem
tfisher.org - document explaining in more detail
14:30 - alternative compensation system
10-digit ID
15:00 taxation
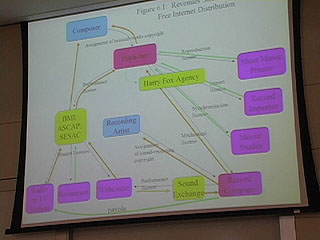
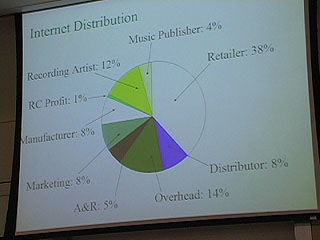
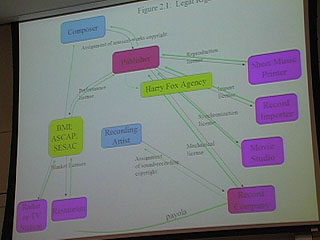
In this presentation, Terry Fisher compares the traditional internet distribution models and explains some of the most important case law surrounding it all including the Sony Betamax case and the Napster case.
Terry Fisher On Music Models - Part 1 of 4 (Small - 39 MB)
Terry Fisher On Music Models - Part 2 of 4 (Small - 39 MB)
Terry Fisher On Music Models - Part 3 of 4 (Small - 50 MB)
Terry Fisher On Music Models - Part 4 of 4 (Small - 50 MB)
Day 3 - Tape 3
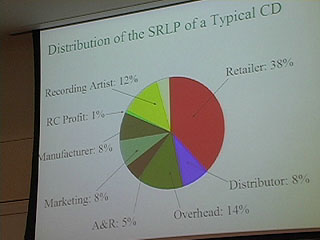
9:00 - comparing old and new CD models
12:00 2/3 of the costs disappear
14:27 Semiotic democracy
18:00 Moral Rights
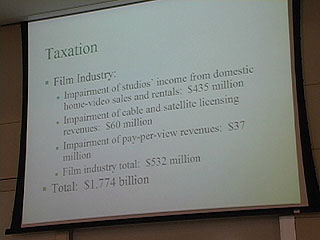
32:00 Good slide on music
35:00 my question about retailers and shelf space
todo: ask about "character provision" of compulsory for covering songs -- note: I never followed up on this - but mean to -- lisa rein
42:40 - movies
45:47 - Fair use and Factors
53:03 - non-infringing uses
Day 3 Tape 4
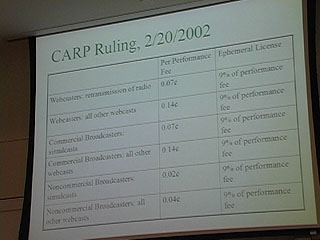
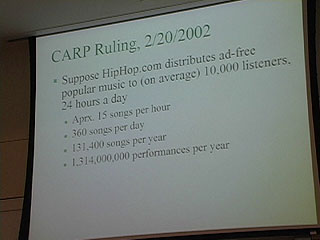
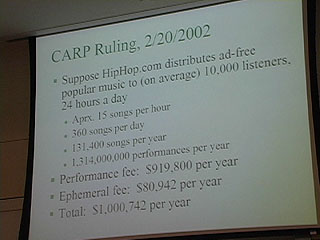
13:34 - CARP
18:15 - Napster
20:00 CD Burning
Here are "small" and Hi-res versions of Zack Rosen explaining the Americans For Dean website. This is taken from the blogging panel that took place on Monday, June 30, 2003 in Stanford, CA.
Zack Rosen At ILaw (Small - 12 MB)
Zack Rosen At ILaw (Hi-res - 167 MB)
This panel also includes a lot of illegal art so I've included it in the appropriate category.
This is a panel featuring Google's Alex Macgillivray, the Electronic Frontier Foundation's Wendy Seltzer and Glenn Otis Brown of the Creative Commons.
Introduction from Larry:
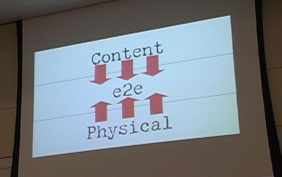
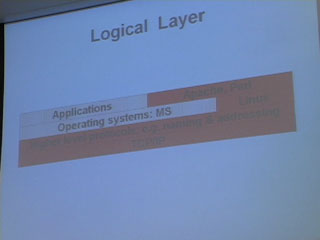
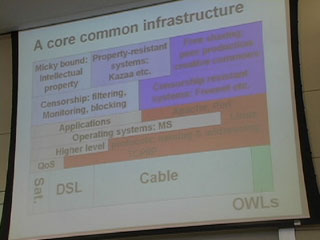
Yesterday, we focused on the physical layer and the logical layer.Today, we focus on the content layer. The content layer has two radically different types of content built into it:
1) Content of MP3s and film
2) Content of programs and applications
Today we will walk through the scope of technology affecting *this* type of content and the law affecting on *this* type of content and the market on *this* type of content.
Charlie Nesson was the host for the panel.
Charlie's Content Panel - Part 1 of 4 (Small - 43 MB)
Charlie's Content Panel - Part 2 of 4 (Small - 39 MB)
Charlie's Content Panel - Part 3 of 4 (Small - 44 MB)
Charlie's Content Panel - Part 4 of 4 (Small - 36 MB)
Just a few notes and lots of pictures for this one. This includes excerpts from the Illegal Art film festival and lots of great media clips from all three guests.
Day 3 Tape 1
8:49 - What is P2P with Alex
9:51 - "Democratization of the space"
11:00 - Napster
13:30 - Charlie Nesson as a supernode
20:14 - Fred
***
Day 3 Tape 2
Cut out part around 13:20 - tech diff
21:45 - Lynne Cheney
25:00 Mention of Howard Dean meetup
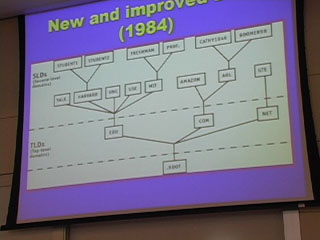
a.k.a - Domain names - How the mess came about
or
"How the Nerds Were Having A Perfectly Good Time Until The Businesspeople And Lawyers Showed Up And Ruined Everything"
This is a tag team lecture by Jonathan Zittrain and Terry Fisher which covers the entire history of domain names from the beginning of the Internet to the present day.
Jonathan and Terry - Part 1 of 4 (Small - 60 MB)
Jonathan and Terry - Part 2 of 4 (Small - 54 MB)
Jonathan and Terry - Part 3 of 4 (Small - 50 MB)
Jonathan and Terry - Part 4 of 4 (Small - 52 MB)
I don't have any notes for this section, but I do have a ton of pictures.

This work is licensed under a
Creative Commons License.
This is a placeholder for the brief panel with former FCC Chairman Reed Hundt and Leslie L. Vadasz, Director Emeritus, Intel Corporation that took place during the first part of Tuesday afternoon at ILAW 2003.
I had only recorded a portion of their presentations and the Q and A afterwards, because I hadn't brought enough tape for the entire day and I didn't want to miss the governance tag team with Jonathan Zittrain and Terry Fisher that was scheduled afterwards.
As it turns out, Reed Hundt asked that I not publish his presentation (which was quite a surprise considering that it didn't seem like he had said anything that could be construed as even remotely controversial).
So this entry is just a placeholder for what would have gone here.
Note: Except for Jonathan Zittrain's introductory presentation (Day 1-AM 1) and this presentation (Day 2 - PM 1), my ILAW 2003 video archive will contain the conference in its entirety.
The most important point:
End to end character of the web.How this was a design choice.
Intelligence is at the edges. Network is simple.
Dominant monopoly can't control/discriminate.
Can't see who people are.
Can't forbid certain uses.This was a fundamental architectural choice.
Larry On End-to-End - Part 1 of 4 (Small - 69 MB)
Larry On End-to-End - Part 2 of 4 (Small - 59 MB)
Larry On End-to-End - Part 3 of 4 (Small - 81 MB)
Larry On End-to-End - Part 4 of 4 (Small - 74 MB)

This work is licensed under a
Creative Commons License.
day 2 tape 3
Larry On End to End Architecture
The end to end character of the logical layer
2:26 - Difference Between AM and FM Radio
4:15 - How Sarnoff Tried to...
AM/FM Radio Backrounder
David Sarnoff vs. Armstrong and RCA
Packet Switching
How AT & T discriminated against any ideas that wouldn't benefit their monopoly.
How competition can be crushed by the dominant network provider.
Excite/AT&T - Dominant cable provider
"Blood sucked from our veins"
9:30 - Innovations that gave birth to the internet
10:50 - All by kids and non-americans
11:52 - Policies and Consequences of Architecture
12:08 - End to end character of the web. How this was a design choice.
Intelligence is at the edges. Network is simple.
Dominant monopoly can't control/discriminate.
Can't see who people are.
Can't forbid certain uses.
This was a fundamental architectural choice.
23:14 - Hourglass model
Note to transcribe some of this...
26:20 - voice over IP
32:15 - Commons - What is a commons
33:30 - Tragedy of the commons
34:30 - rivalrous and non-rivalrous resources
39:40 - Innovation Commons
41:40 - Why the property model makes no sense on the Internet.
How it just doesn't make sense to propertize all resources.
44:35 - Strategic behavior
Competitors do things that benefits them but harms the network
45:40 - Microsoft case - defensive manipulation - note to highlight this
MS stops around 52:00
54:20 - consumer-financial innovation
57:20 - unlicensed spectrum
Day 2 Tape 4
8:00 Media Consolidation
11:00 How the Internet needs to run like the electric network
he mentions my weblog around 12:00
16:20 - Neutral Networks (Note: not "neural" but "neutral"
22:00 - Q and A - why complexity is bad
note: after this point, the numbers are iffy...
27:13 - when property rights aren't appropriate
28:29 - Eldred economists amicus brief - "no brainer."
32:00 - maybe "commons" isn't the right word
not either or but a balance between property and FREE
Eldred wanted to publish his annotated Robert Frost poems.
Note from lisa: people are always asking me what the work was that Eric Eldred was waiting to fall into the public domain that originally brought about the court case. The answer is "Robert Frost poems."
This is from the first session on the second day of ILAW at Stanford, July 1, 2003.
My notes are located beneath the photographs.
Yochai Benkler was as amazing as ever (I've been a big fan since the Spectrum Conference -- note that there's no link there because I still haven't uploaded it...argh...)
Yochai On Architecture - Part 1 of 4 (Small - 62 MB)
Yochai On Architecture - Part 2 of 4 (Small - 62 MB)
Yochai On Architecture - Part 3 of 4 (Small - 50 MB)
Yochai On Architecture - Part 4 of 4 (Small - 16 MB)

This work is licensed under a
Creative Commons License.
Lotsa notes on this one:
Day 2 - Tape 1
7:15 - slide of a communications channel
9:57 - one of the things at stake is democracy
What Terry Fisher explained yesterday as "political democracy"
12:00 QOS Dangers
14:10 - innovation
19:00 architecture for non-techs
28:10 - "Monopoly and a half"
31:25 - Thing that changed from the last 100 years
35:50 - Verizon's competitor division makes more money than the entire recording industry
39:35- FCC notice of inquiry
42:00 intra-modal "competition within the mode of transmission"
"Maybe competition between these modes is all we need?" - Yochai
Duopoly...
44:30 - Do two pipelines a competitive market make?
50:00 - Where "the internet" fits into the cable and telecom
51:20 - where wireless fits in
53:50 - Personal Area Networks
Day 2 - Tape 2 (Yochai continued)
:47 - No owner of the network
-No license required
5:01 - old vs. new world
7:50 - "Mary had a little lamb" - example
Smart receivers and how they work.
10:50 - Processing gain
The use of intelligent receivers
12:20 - cooperation gain
14:30 - repeater networks
How they will work like cellphones.
15:10 - multi-user information theory
multi-user detections
16:20 - Does adding users cost nothing because each user adds their own capacity to the network?
We don't know for sure, yet. But it's definitely possible. (paraphrase)
21:00 - "efficient" use of spectrum can't be defined
23:00 - duopoly
25:28 - Trusted systems
27:25 - could be open or closed
How one can control it all if they control one layer.
35:36 - Version putting wifi in its phone booths in NY
My notes for this session are included underneath the links to the video files below.
I'll be putting up highlight clips for Terry Fisher's description of the three different kinds of democracy, Zack Rosen's presentation on Americans For Dean, and probably a few other exciting moments.
Charlie Nesson put together an ad hoc panel on Blogging and Democracy. Aaron Swartz, Zack Rosen, yours truly, David Hornik, Colin Mutchler, and Frank Field all participated.
Charlie's Panel - Part 1 of 5 (Small - 44 MB)
Charlie's Panel - Part 2 of 5 (Small - 43 MB)
Charlie's Panel - Part 3 of 5 (Small - 38 MB)
Charlie's Panel - Part 4 of 5 (Small - 44 MB)
Charlie's Panel - Part 5 of 5 (Small - 30 MB)
Notes: Day 1 - Charlie's Panel On Blogging As A Tool Of Democracy
Terry Fisher explaining the different types of democracy.
Three primary meanings:
1) Political Democracy - A political system in which we are governed by laws we ourselves make.
Several parts to this:
1) Elected Officials
2) Frequent and Fair Elections
3) Anyone Can Run
4) Freedom Of Expression
5) Information From Alternative Sources
6) Freedom Of Association
2) Economic Democracy
Three parts to this:
1) Workplace Participation
2) Shape Character Of Products
3) Meaningful Work
3) Semiotic Democracy - Widespreade popular participation in the process of making cultural meanings.

From left to right: Colin Mutchler, Zack Rosen, David Hornik,
Aaron Swartz, Lisa Rein, Frank Field and Charlie Nesson.








This work is licensed under a
Creative Commons License.
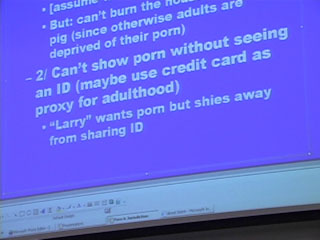
In this session, Larry and Jonathan tag team in order to play devil's advocate across an array of Jurisdictional issues, using the situation of accessing porn over the internet and all of the case law surrounding it as the basis for discussion.
Ack! These links were bad this am - should be fixed now!
Lessig and Zittrain - Day 1 - Part 1 of 5 (Small - 53 MB)
Lessig and Zittrain - Day 1 - Part 2 of 5 (Small - 51 MB)
Lessig and Zittrain - Day 1 - Part 3 of 5 (Small - 51 MB)
Lessig and Zittrain - Day 1 - Part 4 of 5 (Small - 50 MB)
Lessig and Zittrain - Day 1 - Part 5 of 5 (Small - 53 MB)

This work is licensed under a
Creative Commons License.
About these notes and videos -- how the files are named, etc.
Here's Lessig's own description of the Monday morning sessions:
"The point (of Jonathan's session) is to layout some framework for the technology. And the objective of this second part of the morning is to lay out the framework about how to think through these questions of regulation in the context of cyberspace by thinking through a little bit about the question of regulation in real space."
Larry June 30 - Part 1 of 4 (Small - 81 MB)
Larry June 30 - Part 2 of 4 (Small - 81 MB)
Larry June 30 - Part 3 of 4 (Small - 41 MB)
Larry June 30 - Part 4 of 4 (Small - 45 MB)

This work is licensed under a
Creative Commons License.
I don't have any notes for these opening sessions because I was getting aquainted with following Larry around with the camera.
(Jumpy bunch those ILAW folks! -- Larry, Jonathan, Yochai, Terry, Charlie -- the whole lot of them!)
In the afternoon, I actually got to be on a panel so I had to just get a long shot for most of it (although I did end up going back and forth between being on the panel and getting some close ups when the subject matter was to precious and I knew a long shot wouldn't do.
A bit later, after I was able to get used to things, I was able to take notes while filming. You'll know when this takes place because 1) you'll have the notes and 2) you'll start to notice me missing a shot every now and then when my subject bounces out of view momentarily.
So there are trade-offs, but this whole thing's just a big experiment anyway. So it would appear that no harms done.
I would really appreciate your feedback on this footage. Does it work OK? Can you hear everything? Suggestions for next time? All that kind of stuff is duly appreciated.
Oh yeah -- Every clip is numbered in order, by day (1-day1-larry-1of4-sm.mov, 2-day1-larry-1of4-sm.mov, etc.), so you can just watch them all in order if you like.
See more about this in the "How these files are named and organized" section I'll be putting up soon.
This first half of the Monday morning's session is the only session of the conference that I wasn't able to capture on video.
(I hadn't asked if it was OK yet and I felt kind of funny just showing up with a camera.)
Below are my notes...
Notes from the ILaw Conference - June 30, 2003
So I've brought my camera, but I'm sort of waiting for the right time to bust it out.
(Note: since I first wrote this, Larry has given me the OK to tape. So the rest of the sessions will be recorded.)
Until then, you probably want to read Donna's notes, but I'm also going to offer some of my own.
Jonathan Zittrain
Internet Technologies and Why They Matter
I'm prefacing Zittrain's slide language or quotes from his mouth with a "-" to separate them from my notes.
-Code is a powerful form of regulation
-it's subtle
-can't tell when it's regulating you
Example:
The cops were actually directing traffic at the new Crispy Creams opening in Mass.
(Shows where their priorities are.)
-brooks little resistance from the herd
-plastic
-Some current questions:
-Why is it hard to trace people on the Net?
-Why is video streaming such a pain?
-Why are we so vulnerable to viruses and hacks?
-IETF
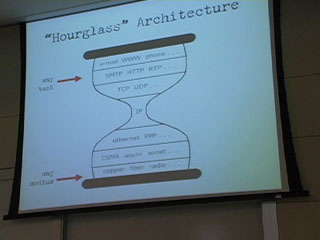
-IETF "Hourglass" Architecture (CTSB, NRC, "The Internet's Coming of Age" (2001)
-"any task" - "email WWW phone...", SMTP HTTP RTP, TCP, UDP
-IP (in the middle)
-"any medium" -ethernet PPP, CSMA async sonet..., copper fiber radio
Kept the physical infrastructure out of the loop on purpose. The people that do wires can do that. Medium independent for a wide range of media.
At the top of the hourglass are the "applications." Network-aware applications. The point was to allow any kind of application to come about without having to know anything special about the network.
The IETF hums for rough consensus. We did a hum in the room on whether or not we understood what he was saying so far so we could see such a strategy in action.
So no force of law, but an agreement among technologists.
-W3C - how HTML was born.
-The birth of Gnutella
-"Network Neighborhood On Steroids"
-The lesson of the Internet is that efficiency is not the primary consideration. Ability to grow and adapt to changing requirements is the primary consideration.
-This makes simplicity and uniformity ....(ack! he switched slides....you get the message)
Jon Postel - IANA - Internet Assigned Numbers Authority
-Amish barnraising theory of packet transport
-your packet goes to an ISP
-ISP might have an ISP
-this goes on with the russian dolls
-routing packets is just the neighborly thing to do
-you pass on mail with your router even if it isn't for you
-no one to complain to when mail doesn't make it
-persistent problem today
-video streaming model
Lisa Reminds you guys to always download my movies and not try to stream them. Even on a T1 :-)
routers know where to send everything...
-not like fed ex, where everything goes through atlanta.
-this is why the IP addresses are in blocks
different ranges are in different parts of the world so the routers don't have to know exactly where everthing is
-this is why IP addresses are "non-portable"
Now Jonathan is trying to check an email to trace where it came from
So he's starting out with one of those fake AOL emails that tell you to enter your credit card information.
He's looking up the IP address (after getting it from the email header using "traceroute" at the command line)
MAPS is a list of "bad" email IP distributors -- so email administrators can use to "blackhole" certain blocks.
He doesn't get that far. Manages to figure out it was sent from Bulgaria.
Question: How do you get connected to the MAPS?
Answer: If you are an ISP, MAPS for a small fee, will provide you with this service.
You can't just get there whole list. You have to ask an address at a time.
-"You cannot build a corporate network out of TCP/IP." - IBM 1992
-What's Missing?
-quality of service
-accounting and traffic management
-encryption and security
-accounting and traffic management
who pays for what? should it be like the telephone where "caller pays?" very difficult to get a business model.
who's benefiting who more?
-encryption and security
This was something that either relies on the good graces of others...
Routers had to learn to deal with misconfigured computers.
One solution is "end to end." Presume the network will be open. That way you don't have to trust everybody along with way.
-authentication
Knowing that the bucket contents you got came from the place you think it came from
a way to let you know when tampering has taken place (can't prevent it ahead of time)
Question: what does this system cost? How much does the internet cost?
Answer: I have no earthly idea.
Question: How bout equipment costs?
Answer: Well, routers aren't cheap... This is a tough question because it's such a decentralized network.
Graham Freeman - My van can connect to the internet when I flick a switch for about $1500...(paraphrased)
Terry Fisher: Could you say a little bit more about what happens in the Cloud?
(paraphrase - we started out with the Amish and ended up talking about "tier 1 providers." how'd we get there (in the discussion)?
Answer: You're right that there's only a handful of Tier 1 internet providers...
Question: How does the bucket brigade work?
Answer: Roughly speakin the network topology maps on to the geography.
(paraphrase) AOL is the Fed Ex of the internet in that, on dialup, everything goes through a central connection.
Question: is there "smart routing"? - routing that takes in to account when a server is busy(paraphrased)
Barbara Roseman ICANN -
Before I was with ICANN I was with "Global Crossing", one of those T1s that didn't disappear.
(paraphrased) Yes there are paths (on the same network) that they know to take for certain geo areas.
So not over the internet, but within a network you might configure your routers in this way.
Questions: I was hoping you could talk more about the physical lines...
Answers: I'm sorry, security considerations stop me from doing that....(chuckles)
(para) the hourglass makes that transparent (basically)
Caida.org - has "skitter" graphs.
My question: Does Sealand (link) function as a Mae West of sorts?
Answer (para) - no not at all. It's just a data store.
question: so it could actually put more strain on the network?
answer (para) - yes they have to buy their connectiving from someone else...
Encryption in 3 easy steps:
1. "Hello" (is the message) - convert the letters to numbers
2. share password ahead of time with the person receiving the message
H 8 I 9 17
E 5 L12 17
L 12 A 1 13
L 12 W 23 35
0 15 Z 26 41
this is uncrackable.
-old style way of encrypting stuff.
-key has to be same length as original data.
we had to get together secretly and share the key first.
Enter "Pubic Key Encryption"
-Task is to find a one-way function (computationally speaking - function where it is really easy to start one thing and get to another), but for which (computationally speaking) it is hard to do the reverse.
-multiply like lightning, but factor only slowly
-find a one way function
-generate two related keys of one person's use
-declare one key "public key" and the other one "private"
-data + public key = garbage no one can read by no one except someone who has your private key too.
Might want to use your dig signature and PGP key to encrypt and vouch for a message.
-Digital Signature - personal to the very thing being encrypted
-To digitally sign something - to vouch for it "could have only been generated by someone who has access to my private key"
Last question: why viruses so hard?
PC ready to run software.
Most viruses just want to replicate, not erase your hard drive. These are like missles without payloads. The damage to the network is from being clogged up.
Primary reason is that "general purpose computing devices" are meant to run anything, so, they do.
(para nutshell) Because software is coming from so many sources. Sometimes the software can't work with each other.
End of notes for this session -- and end of all notes for me because Larry said I can video the rest of it!
(I actually do take notes later...)
No ILAW or any other goodies until it's back up.
I'll be crunching away until then -- so there will be lots to upload when I am able!
(Already have the first session with Larry in the kitty...)
Okay so there's good news and bad news.
The good news is that Larry is letting me film ILAW!
The bad news is that, with me recovering from a cold, an hour commute each way for five days straight, and my having to stand up for most of the sessions (because they get kind of exciting and I have to move the camera around alot between the audience and speakers to get the best coverage of everything), I won't be pulling any late nighters trying to get any of this footage to you before the weekend.
So for now, you should read Donna Wentworth's Coverage and know that it will all be online in due time.
(Yes all five days' worth.)
Cheers!